Massive npm Hack Shows How One Phishing Email Shook the Open-Source World
The npm Hack: How a Single Phishing Email Put Billions of Downloads at Risk
If you think the biggest cybersecurity threats come from ultra-sophisticated exploits, think again. Sometimes, all it takes is one carefully crafted phishing email. That’s exactly what happened in early September 2025, when a hacker tricked a respected open-source maintainer into giving up access to his npm account. Within hours, 18 widely used npm packages were swapped out with malware designed to steal cryptocurrency.
This incident may go down as one of the most significant supply chain attacks in npm’s history—not because of how advanced the malware was, but because it revealed just how fragile the software ecosystem really is.
What Happened in the npm Hack?
On September 8, 2025, security firm Aikido discovered suspicious behavior inside npm package manager, the world’s largest package manager for JavaScript. Their investigation revealed that 18 npm packages had been compromised. Collectively, these packages are downloaded over 2 billion times every week, making them an essential part of modern web development.
The attacker didn’t break through firewalls or exploit complex vulnerabilities. Instead, they sent a fake security email that looked like it came from npm. The email urged the maintainer, Josh Junon, to update his two-factor authentication. In reality, the link redirected him to a lookalike domain (npmjs[.]help). By entering his details, Junon unknowingly handed over the keys to his account.
With access secured, the attacker replaced legitimate versions of the libraries with malicious ones. The injected code attempted to hijack cryptocurrency transactions by silently redirecting payments to wallets controlled by the hacker.
Quick Facts: npm Hack at a Glance
To make the scale of this attack easier to understand, here’s a breakdown of the key details:
| Key Point | Details |
|---|---|
| Date of Discovery | September 8, 2025 |
| Number of Packages Affected | 18 |
| Weekly Downloads Impacted | Over 2 billion |
| Attack Method | Phishing email posing as npm security alert |
| Maintainer Targeted | Josh Junon |
| Malware Goal | Redirect cryptocurrency transactions to attacker-controlled wallets |
| Severity Assessment | Aikido called it the “largest supply chain compromise in npm history” |
| Community Response | Packages were quickly flagged and removed before widespread damage occurred |
Why This Attack Matters
On the surface, this might look like just another cyber incident. But dig a little deeper, and the implications are far more serious.
- Massive Reach – npm is the backbone of backbone of modern JavaScript development When a popular package is compromised, the ripple effects can reach millions of apps and websites in a matter of hours.
- Simple Yet Effective – This wasn’t a zero-day exploit or a nation-state attack. It was phishing—a tactic as old as the internet itself. The simplicity is what makes it scary: if it worked on a seasoned maintainer, it can happen to anyone.
- Trust at Risk – Developers rely on open-source software with the assumption that maintainers keep it secure. When that trust is broken, even briefly, it shakes confidence across the entire ecosystem.
- Crypto as a Target – The injected malware focused on cryptocurrency theft, which makes sense given the fast payoff for attackers. But this also shows that financial systems integrated with code libraries are increasingly becoming prime targets.
Security Community’s Response
The good news is that the community responded quickly. Security researchers, npm maintainers, and other ecosystem defenders acted fast to flag and remove the malicious packages.
Noted cybersecurity expert Florian Roth described the attack as serious but noted that the malware itself seemed “amateur-grade.” In other words, the attacker had access, but their technical skills were limited.
Still, this doesn’t minimize the risk. As security firm Socket explained:
“All it takes is one compromised maintainer for the malware to spread downstream.”
That’s the real problem: one small crack in the chain can impact thousands of developers and organizations who depend on those libraries.
The Bigger Picture: Lessons from the npm Hack
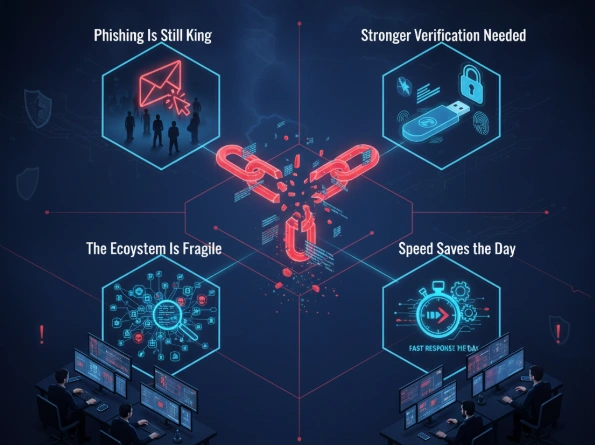
So, what should developers and companies take away from this?
- Phishing Is Still King
Even with advanced security tools, phishing remains the easiest way to break into critical systems. A convincing email is often more dangerous than a piece of malware. - Stronger Verification Needed
Package maintainers need better protection—like mandatory hardware keys or stronger identity checks—to prevent takeovers. - The Ecosystem Is Fragile
Open-source software is incredibly powerful, but it’s also vulnerable. Most developers install libraries without ever reviewing the code. That trust can be weaponized. - Speed Saves the Day
The community’s fast reaction prevented a much larger disaster. This shows the importance of active monitoring and quick incident response.
How Developers Can Protect Themselves
If you’re a developer or organization using npm packages (which, let’s be honest, is almost everyone in the JavaScript world), here are some steps you can take:
- Enable Two-Factor Authentication – But only through official channels. Always double-check URLs before entering credentials.
- Use Package Locking – Lock dependencies to known safe versions instead of blindly upgrading.
- Verify Maintainer Updates – Keep an eye on sudden version changes from libraries you depend on.
- Add Security Tools – Tools like Socket, Semgrep, or GitHub’s Dependabot can catch suspicious behavior early.
- Educate Teams – Security awareness training can stop phishing before it succeeds.
Conclusion
The npm hack wasn’t the most advanced cyberattack in history, but it may be one of the most revealing. It shows that our software supply chains—no matter how modern or sophisticated—are only as strong as the people maintaining them.
Billions of downloads depended on the judgment of one developer, and a single phishing email was enough to bypass every technical safeguard. That’s a chilling reminder for all of us.
The question now isn’t whether this will happen again—it’s when. And the best defense isn’t just better tools, but better habits: vigilance, verification, and community accountability.
FAQs
1. What is the npm hack?
The npm hack refers to a September 2025 incident where a hacker tricked an open-source maintainer into giving up his account credentials through a phishing email. The attacker then uploaded malicious versions of 18 popular npm packages, aiming to steal cryptocurrency from unsuspecting users.
2. How did the attacker gain access?
The attacker sent a fake email that looked like an official npm security alert. It asked the maintainer to update his two-factor authentication. Instead of going to npm’s real site, the link led to a lookalike domain. When the maintainer logged in, the attacker captured his credentials.
3. Which npm packages were affected?
Eighteen npm packages were compromised. While the exact list varies, these were common JavaScript libraries used for everyday tasks like text formatting and font conversion—packages with billions of weekly downloads.
4. Was any major damage done?
Fortunately, the malicious versions were online for only a short time, and the community acted quickly to remove them. That means the overall damage was limited, but the potential risk was huge.
5. Why was cryptocurrency the target?
The injected code was designed to intercept crypto transactions and redirect funds to wallets controlled by the attacker. Cryptocurrency is often targeted in hacks because it’s fast, hard to trace, and can be converted into cash quickly.